
Overview
Tencent Cloud Web Application Firewall (WAF) helps internal and external Tencent Cloud users fight security issues such as web attacks, intrusions, exploits, trojans, tampering, backdoors, crawlers and domain name hijacking. By deploying WAF, corporate users can redirect the threat and pressure of web attacks to the protection cluster nodes of WAF, obtaining the web business protection capabilities of Tencent Cloud in just minutes to safeguard websites and secure operations of web businesses.
Benefits
AI+ Web Application Firewall
Virtual Patches for Zero-day Vulnerabilities
Webpage Tampering Prevention
Data Leakage Prevention
CC Attack Prevention
Crawler and Bot Behavior Management
DNS Hijacking Detection
Features
- Industry-leading AI+ Rules and Dual Engine
- Integration with Tencent's Big Data-based Threat Intelligence
- Virtual Patches for Vulnerabilities
- Proprietary AI-based Crawler and Bot Behavior Management Module
- Proprietary DNS Hijacking Detection Module
- Data Leakage Prevention
- CC Attack Prevention
- Webpage Tampering Prevention
- Custom Protection Strategies
- One-click Integration with High Defense Capabilities
- Fast and Reliable Protection Experience
Scenarios
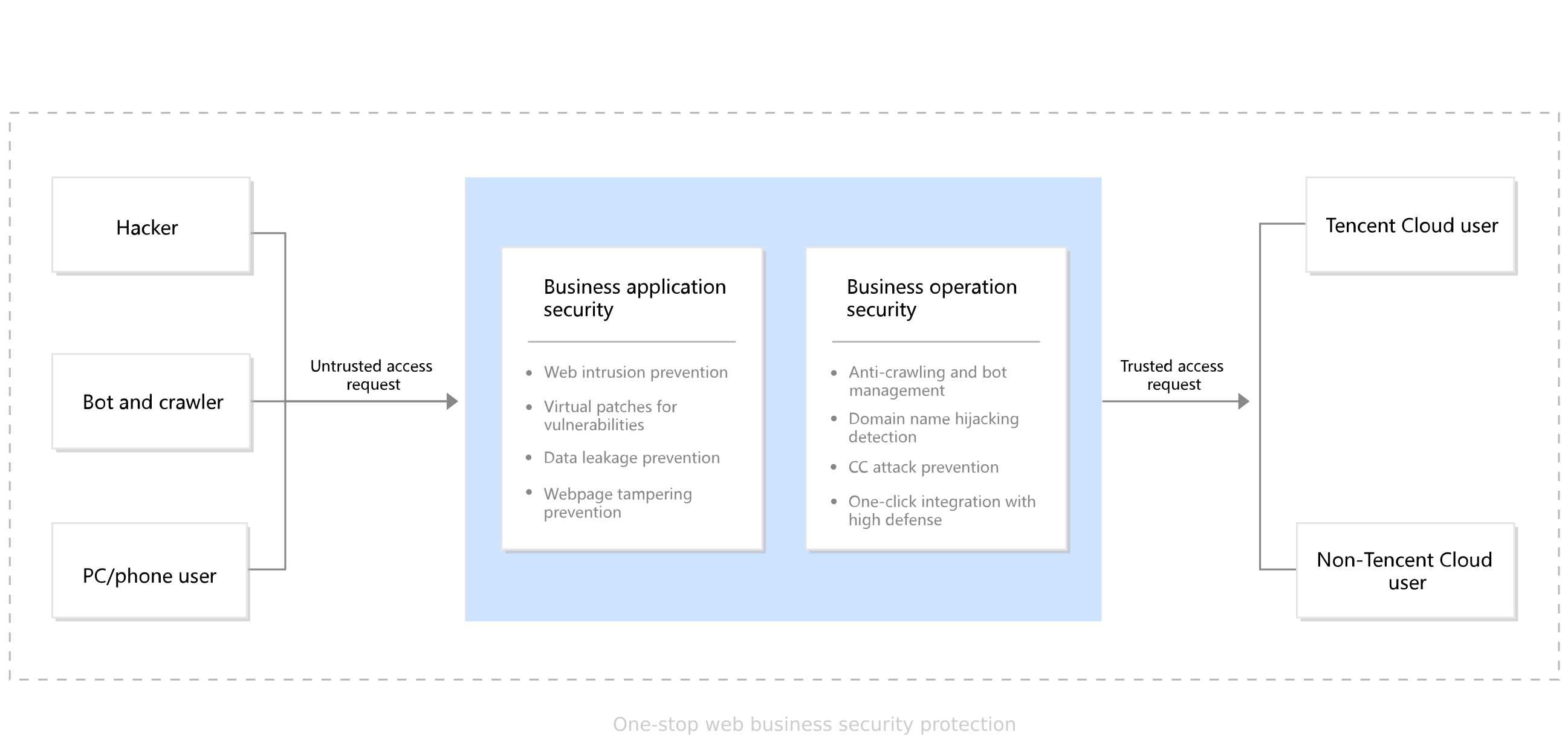
WAF protects business data from being intruded on, tampered with and stolen and filters out all kinds of attack and spam traffic, supporting the normal and stable operations of core Internet+ businesses.
It eliminates the negative impact of various issues caused by malicious bots, such as copyright infringements, malicious SEO, data crawling and leakage and spam traffic.
It features high availability and elastic scalability based on business size and reduces protection costs.
- Internet+ Businesses
- O2O Ecommerce Websites
- Finance Websites
- Government Service Websites
- Corporate Websites
WAF protects business data from being intruded on, tampered with and stolen and filters out all kinds of attack and spam traffic, supporting the normal and stable operations of core Internet+ businesses.
It eliminates the negative impact of various issues caused by malicious bots, such as copyright infringements, malicious SEO, data crawling and leakage and spam traffic.
It features high availability and elastic scalability based on business size and reduces protection costs.

